[solved] how to fix the SAML error for AWS and ADSF IAM integration – Response signature invalid (Service: AWSSecurityTokenService; Status Code: 400; Error Code: InvalidIdentityToken
This article is only relevant when you have on ADFS setup with your AWS account for role mappings and authentication. The HTTP error code 400 is what you get when trying to authenticate and it does not go past the login page.
You can capture the full saml response in the saml decoder if you have one installed
you can the Google saml decoder by going to the link below
you can then go the login page and try logging in and then this will capture all the details and you can see if the correct certificate is pushed out via ADFS – in order to match the certificate you can go AWS – IAM and then go to identity provider and download the metadata file and then you can match what is in the metadata file in AWS needs to match the metadata file in ADFS
below is screenshot of AWS IAM Page where the metadata file can be downloaded
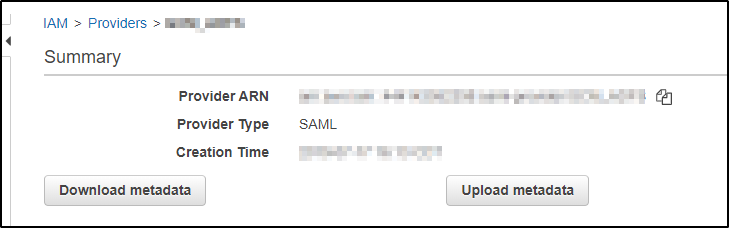
and below is the screenshot of what we are looking for in the saml decoder to make sure it matches
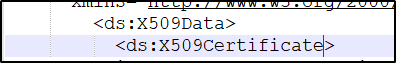
In this case ADFS rotates the certificate yearly and the fingerprint was not matching with the destination identity provider
You can download the new ADFS metadata file by going to the following link and replace “adfs-server.domain.com” with your server fully qualified name and this should have the updated certificate –
https://adfs-server.domain.com/FederationMetadata/2007-06/FederationMetadata.xml
Go the the link and download the new metadata.xml file and upload to the destination identity provider whether AWS or any other vendor
below is where you would upload for AWS by going to IAM and then Identity Provider on the left and choosing the one in question
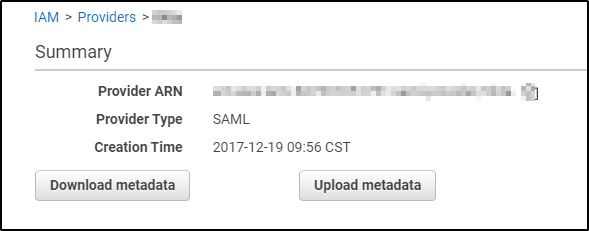
Hope this helps




