
- Knowledge is power
- The Future Of Possible
- Hibs and Ross County fans on final
- Tip of the day: That man again
- Hibs and Ross County fans on final
- Spieth in danger of missing cut
Setup
PulseSecure VPN appliance is setup for authentication using AzureAD SAML. AzureAD is the IDP for users logging into the PulseSecure appliance.
Problem
Users are getting the error message when trying to login using SSO with AzureAD and getting the below error message “no valid assertion found in the SAML response” – see the screenshot below for the exact error message screen.
Solution
This seems to be an issue with many versions of the code with PulseSecure. the issue is caused with NTP settings where the click is skewed, the workaround is to remove the NTP settings and manually set the time.
- here is how you can setup the time manually and remove the NTP server settings
- Click on Systems and status
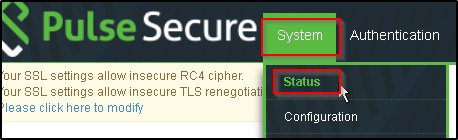
- Once on the status page then click on “Edit” to change the settings
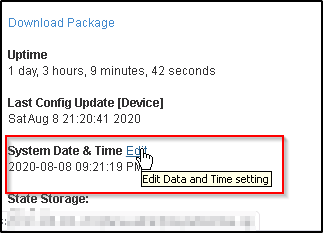
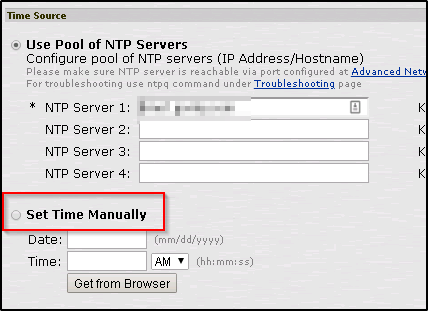
- You can see if the appliance is set to use the NTP server if that is the case then you can uncheck “use Pool of NTP servers” and check “Set Time Manually”. this will set the time on the appliance manually and it is also a recommendation by PulseSecure support to keep the NTP disabled if using SAM configurations
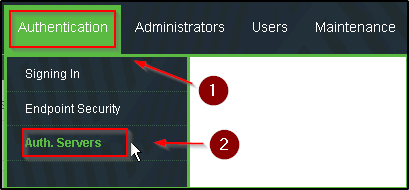
- Go to the “Authentication tab and click on the Auth Servers – see the screenshot for reference
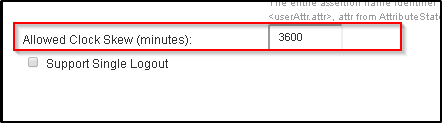
- Once you have clicked on the Auth Servers then pick the SAML and double click the server to edit the settings
- You will need to change the settings for “allowed clock skew (minutes ) and you can set that to 3600 and that should fix the login issue.
you can test the login now using different browsers and it should work as expected.
Thanks for reading this and I hope this was helpful. below is the link to some KB articles with related SAML issues.


