[Solved] how to configure and install Cisco vASA firewall on an ESX host step by step for VMWare.

Now that we have COVID19, the need for remote access is greater than ever and without access to the physical site, the best way to deploy a firewall is doing it virtually. The nice thing is that Cisco has made the firewall available for everyone free for three months. see the picture below for details.
The Cisco vASA 50 will support 10K VPN remote access connections. Cisco ASA’s are rock solid firewalls that provide consistent user experience.

Ok, lets see what needs to be done to get that up and running.
what is prerequisite for the firewall setup.
- ESX host with virtual switches for the inside and outside interfaces/vlans.
- Cisco CCO account to download the software.
- Public IP addresses for the outside interfaces
login into the Cisco support site to download the software.
you will need to go the site and download the firewall software. see the package for the VMWare.
Once the file has been downloaded then you can extract the file since downloaded file format is .zip in the location to have .ovf ready to be deployed.
Once you have downloaded the software then you will need to deploy the OVF .
- Browse to the files
- Select the 4 files
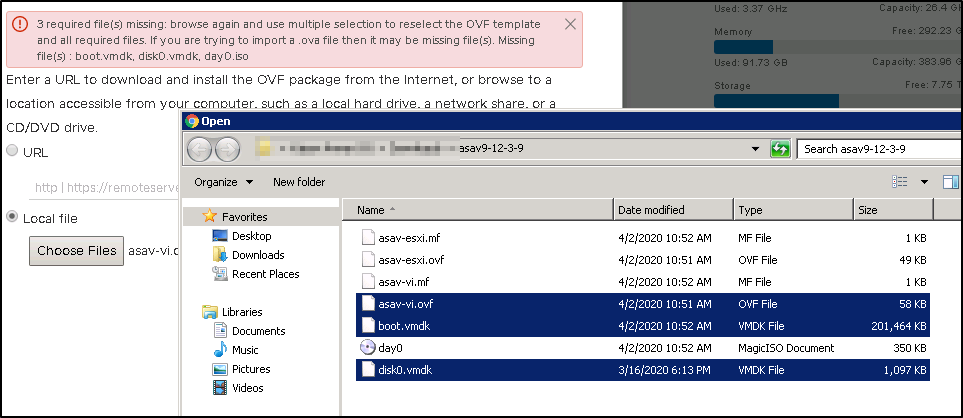
You can now see the 4 files are now selected. click on next to continue to the next screen.
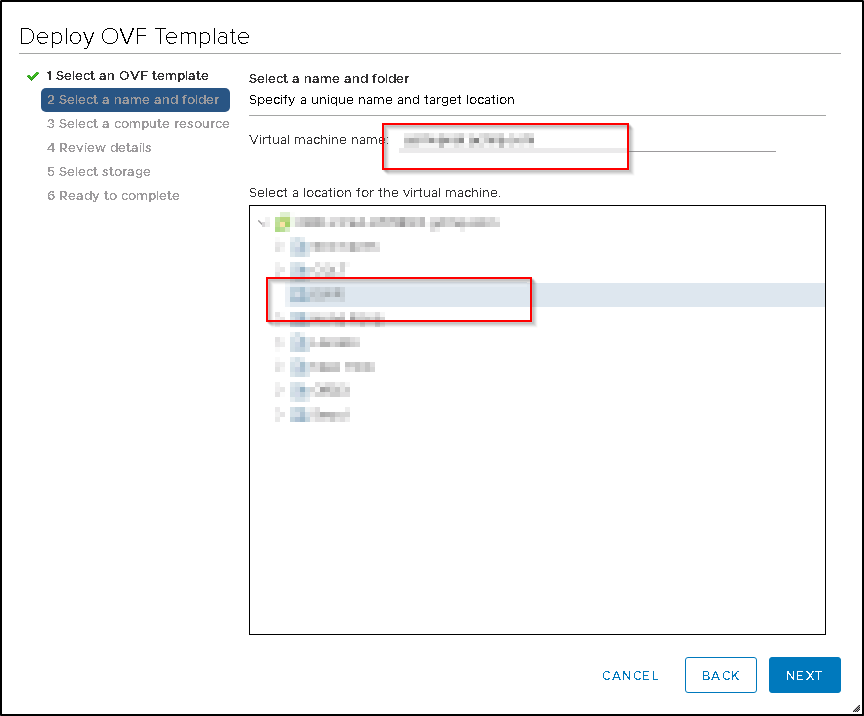
- Name the Firewall
- select the location of the firewall.
Confirm all the details and click on Next to continue to the next screen.
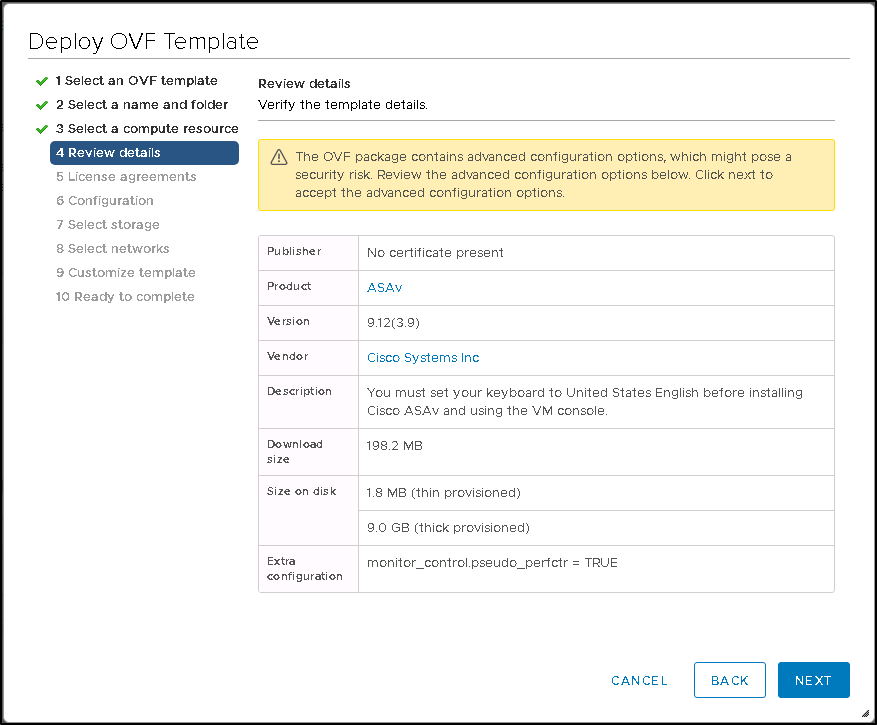
here you will need to select the virtual switches and one has to be internet facing and one should be facing on the internal network.
see the picture for reference.
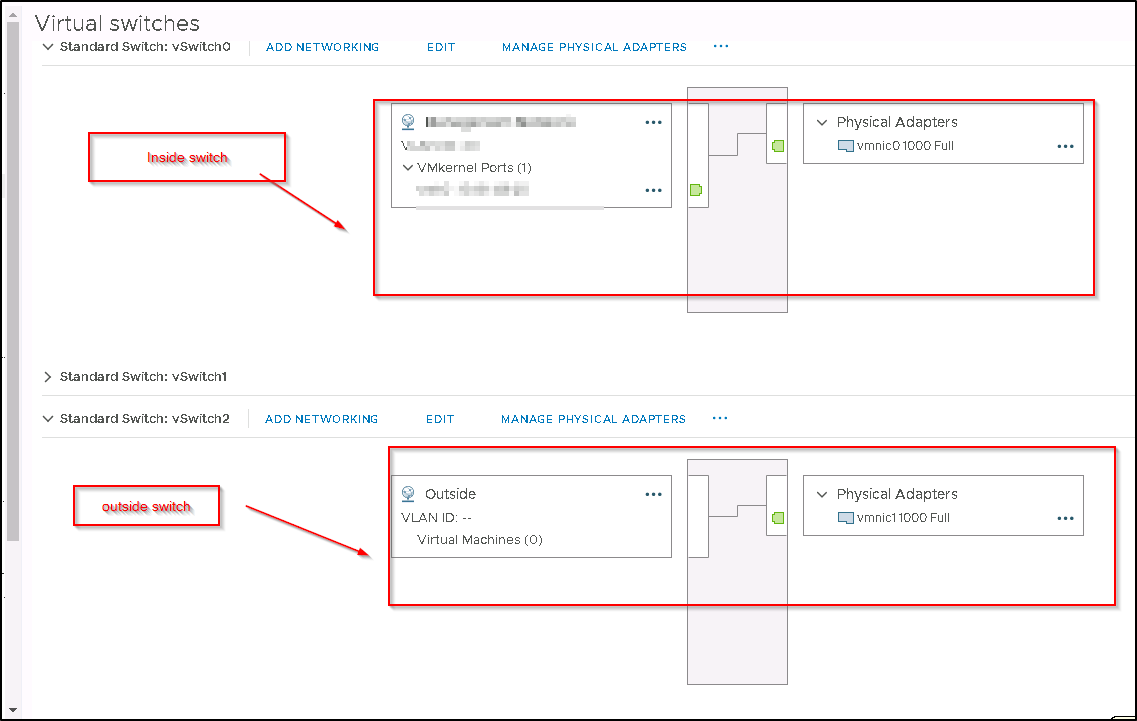
The screen below has quite bit of settings where you can choose your HA pair or single firewall setup. I have chosen the HA pair.
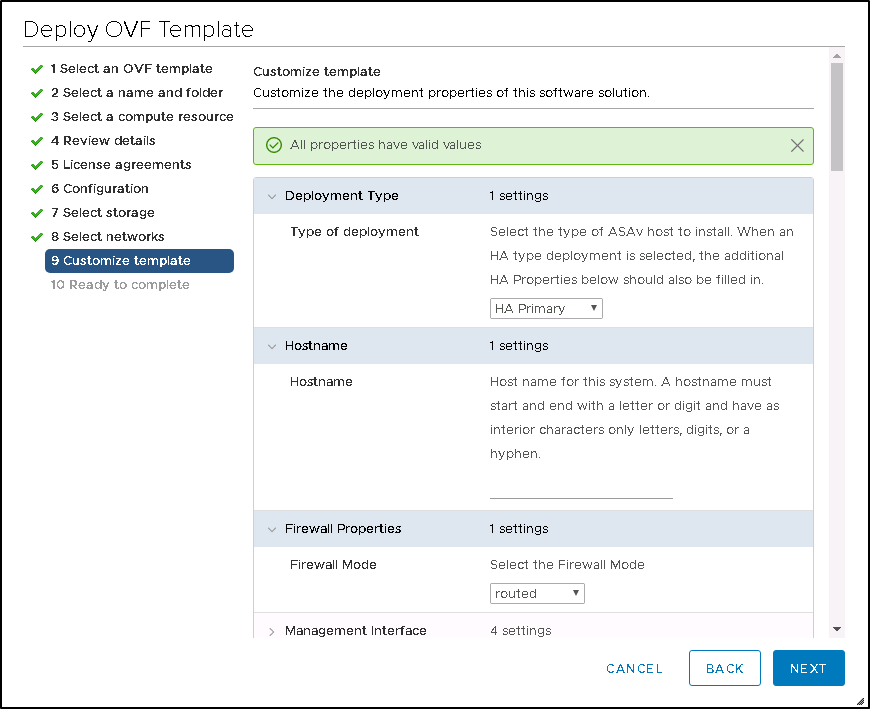
This is your failover interface for the failover sync traffic. once finished click on finish to deploy the appliance.
The appliance is now deployed
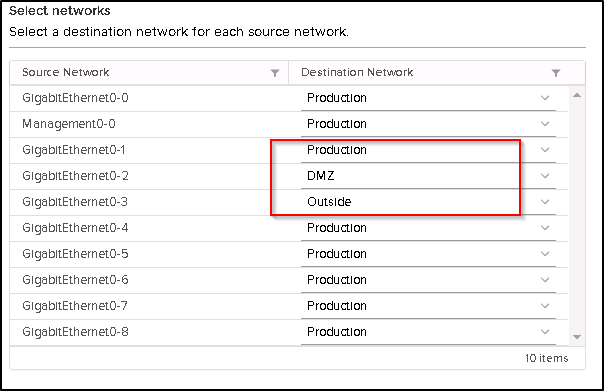
Please note that each network card is connected to separate virtual switch with a separate VLAN.
- Production should be your “inside” interface security 100.
- DMZ should be where you can host your public facing web server with security of 50.
- Outside is the less secure with public ip address and has a security of 0.

You now should be able to power up the VM.

